Microsoft offered virus writers yet another wonderful chance of frustrating millions of PC users. The latest security flaw, incorporated in every OS based on the NT4.0 core (or later), enables a ”Run code of attacker’s choice”, as you can find in the Microsoft Security Bulletin MS03-026.
These versions of Windows allow a buffer overrun in the RPC (Remote procedure call, follow link for more information) part of Windows’ DCOM service. Due to this overrun, the buffer is no longer just used as data storage, but executed as code…
Microsoft offered virus writers yet another wonderful chance of frustrating millions of PC users. The latest security flaw, incorporated in every OS based on the NT4.0 core (or later), enables a ”Run code of attacker’s choice”, as you can find in the Microsoft Security Bulletin MS03-026.
These versions of Windows allow a buffer overrun in the RPC (Remote procedure call, follow link for more information) part of Windows’ DCOM service. Due to this overrun, the buffer is no longer just used as data storage, but executed as code.
The flaw was discovered by the The Last Stage of Delirium Research Group. Microsoft acknowledged the problem, and released information about the flaw on 16 July 2003. After that, a virus writer saw his chance, and started a plague.
The newest wide-spreading virus is called W32.Blaster.Worm (Symantec), W32/Lovsan.worm (McAfee), W32/Blaster-A (Sophos),WORM_MSBLAST.A (Trend micro), W32/Blaster (Panda), Lovesan (F-secure). Most often rated virus as posing a medium overall risk, some estimate higher risks (eg. F-secure).
The world doesn’t sleep, and already reacted to the first version of the virus. Our programmer doesn’t sleep much neither, as he’s releasing new variants of the virus. Sophos antivirus reports a new version of the virus as well, called W32/Blaster-B. F-secure already covers a ”C” version of the virus. I think we can expect more variants during the following week.
Regarding the damage caused by this virus: Symantec raised their levels of alert due to the amount of infections. If the inquirer is right, IBM got infected as well.
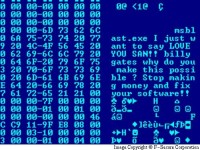
The virus source contains the following message (according to Sophos, F-Secure):
|
|
Version A:
I just want to say LOVE YOU SAN!!
billy gates why do you make this possible ?
Stop making money and fix your software!!
Version B:
Microsoft can suck my left testi!
Bill Gates can suck my right testi!
And All Antivirus Makers Can Suck My Big Fat Cock
Although the first version looks like the author meant it well (just pointing at the seriousness of this problem, and the ever lasting security problems Microsoft has), it turns out differently:
| How it works |
It enters your pc using the RPC flaw: scanning from TCP port 135, it searches new victims, using an algorithm that chooses which IP’s are targeted (F-Secure and Norton have a explanation of the mechanism of IP choosing).
One out of five searches is targeted towards Win 2k users, the other 4 are against Win XP users; Win NT/2003 servers could crash, they don’t get infected.
When another vulnerable pc is found, it uses TCP port 4444 to create a remote shell in the target computer, and downloads itself after the target did send a TFTP UDP port 69 command. During these operations, you can get error reports from svchost.exe, when the information send by the virus was not correct. Due to the amount of traffic generated, you could end up with an over saturated network.
MsBlaster is saved in your windows directory and executed. The program is saved as ”msblast.exe” (original virus), Root32.exe and teekids.exe (first variant) and penis32.exe (second variant). It starts listening to 20 TCP ports (constantly changing, the 20 ports follow each other), although the function of this hasn’t been found yet. >
After that, it creates a registry key in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run with the following value: ”windows auto update” = msblast.exe. By doing this, it makes sure it is executed every time you start Windows.
When you start windows, a system shutdown message is displayed, giving you exactly 1 minute to work on your pc (guess you don’t have to try 3Dmark then :p). This message is generated by windows, so it can appear in any language you use. The reason for this message is that the virus makes RPC to crash. As this is a critical service in Windows, your OS tries to restart it, but unfortunately that is only possible by rebooting.
|
Between 16 and 31 august of January to august, it also tries to launch a massive DoS attack on Microsoft’s Windows update site, disabling you (and the site) to get a patch. (And probably pull their servers down for a while as well).
The virus (as far as we know at this moment) doesn’t destroy data, nor does it enable access to your pc, it just gives you a bad time until you find a suitable fix.
There are three options:
-
Using your updated virus scan
-
Delete the worm manually
-
A lot of antivirus companies also have a tool available (listed here):
If you want to kill it manually (sweet revenge?), these are the steps you should take (described for the original virus): (Note: do this on your own risk!)
- Make sure your computer doesn’t shut down before you can take further actions:
- Go to start menu – run
- type ”shutdown /a”
- Disable system restore
- Start in safe mode
- Go to control panel (classic view if you are using Win XP)
- Open ”System”
- Go to the system restore tab, and disable system restore
- End the virus using Task Manager
- Press Ctrl+Alt+Del
- End the maxblast.exe process
- Delete the registry key
- Open regedit (start menu > run > regedit)
- Search for the following key: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- On your right side, you will see the value ”windows auto update”=”msblast.exe”. Delete this.
- Delete msblast.exe from your Windows directory.
- Prevent the virus from ever infecting you again
You can protect your computer by downloading the latest patch (available for all affected OS’es) from here. This site also gives information about configuring your windows firewall (either the one embedded in XP/2003, or a few commercial options) to prevent Msblaster to infect your pc. Since this virus is not a part of the Klez family (which shuts down virusscanners for you), a working and updated virusscanner could be a solution as well.
To conclude this article, I’d like to advise everybody to make updating your Windows version a habit. You could do this manually, or go for an automatical version, which Windows XP enables. Although Microsoft have their ”trustworthy computer initiative” to find and kill security flaws in their products, they’re still far away from being the provider of stable and secure programs. Patching you programs will always be a part of your relation with Microsoft.
If all of this becomes too much for you, there are still open source alternatives available. I suppose there are security flaws in Linux as well, but at least they are not so obvious as those in Windows.
If you want more information about this virus, you can always check the sites of any virus scanner. They all got at least one page about this virus. There’s also a dedicated page about the worm which you can find here.
UPDATE:
- On this site made by Microsoft you can find links to all the information they provide about the worm. They also recommend home users to do the following 4 steps: install a firewall/configure an existing one, update Windows, get a virusscanner and remove the worm. What strikes me is what they choose ”Remove the worm” as fourth step: Looks like they have other priorities than I do.
- The Inquirer, as well as [H]ardOCP or News.com tell us that the domain www.windowsupdate.com would be killed by Microsoft. This appears to be true, the site is currently unavailable. So nice of Microsoft to tell us about it X-( …
- Keptech.net have made a removal tool, which you can find here.
Two more updates:
- Reuben Chew, the maker of the dedicated worm site made a tool, which you can download from his site.
- There is a new worm around; although the idea of virusses and worms is repulsive, this is a nice one; it tries to update your pc, and to remove blaster if your pc was infected. That’s the positive part. The negative is that you get… an other worm. You can read more about this virus here